Explore other categories
- Aplikácie (3)
- Linux (2)
- ATM (21)
- ATM Linux (4)
- Hardvér (6)
- ForeRunner LE155 (5)
- ATM (28)
- Cloud (3)
- Cloud services (1)
- MicroStack (2)
- ENUM (2)
- Generátory prevádzky (4)
- H.323 (2)
- Hardvér (1)
- IDS/IPS (2)
- Instant messaging (4)
- Instant messaging (4)
- IP QoS (5)
- IP QoS (1)
- References (1)
- Tools (1)
- IP Telefónia (10)
- VoIP (4)
- IP Telephony (6)
- VoIP (3)
- IPTV (1)
- IPTV (2)
- IPv6 (6)
- Tools (2)
- IPv6 (2)
- KNIHY (6)
- Linux – AkoNaTo (34)
- Linux – HOWTO (52)
- Monitoring, Management, Measurement (11)
- Monitoring, Manažment, Meranie (14)
- NetAcad (7)
- NetAcad (22)
- Network security (27)
- Network simulation and modelling (22)
- Dynamips/Dynagen (1)
- GNS3 (15)
- Opnet (1)
- Packet Tracer (1)
- UNetLab (3)
- NGN/IMS (6)
- Kamailio IMS (2)
- OpenIMSCore (3)
- NGN/IMS (23)
- Kamailio IMS (16)
- OpenIMSCore (5)
- Packet captures (8)
- Portál (8)
- Practical – Cisco (34)
- Practical – Juniper (1)
- Practical – Fortinet (2)
- Fortigate (2)
- Practical – Mikrotik (2)
- Prakticky – Cisco (24)
- Sieťová bezpečnosť (24)
- Sieťové simulácie a modelovanie (30)
- Dynamips/Dynagen (1)
- GNS3 (7)
- Opnet (10)
- UNetLab (1)
- VNX (1)
- SIP (126)
- Aplikačné servery (15)
- Mobicents (13)
- Asterisk (12)
- Bezpečnosť (5)
- FreeSWITCH (1)
- Iné SIP Servery (12)
- SER (2)
- Kamailio (10)
- Nástroje (8)
- NAT, FW (3)
- OpenSER (15)
- OpenSIPS (1)
- SIP referencie (4)
- SIP UA (25)
- SipXecs (5)
- Služby (6)
- CPL (4)
- Testovanie (3)
- Aplikačné servery (15)
- SIP (75)
- Application servers (1)
- Asterisk (3)
- FreeSWITCH (2)
- Kamailio (29)
- NAT, FW (5)
- OpenSER (2)
- OpenSIPS (2)
- Other SIP Servers (1)
- Security (1)
- Services (6)
- CPL (3)
- SIP Availability (2)
- SIP references (2)
- SIP UA (10)
- SipXecs (2)
- Testing (2)
- Tools (10)
- TCP/IP networks (2)
- Tools (2)
- Theses (2)
- Traffic generators (1)
- Virtualizácia (7)
- OpenStack (2)
- VirtualBox (3)
- Vmware (1)
- Vmware images (1)
- Virtualization (14)
- VirtualBox (13)
- VB images (2)
- XenServer (1)
- VirtualBox (13)
- Vyučovanie (1)
- WebCMS (9)
- Drupal (3)
- Joomla! 1.5 (5)
- Komponenty (1)
- Plugin (1)
- WebCMS (1)
- Drupal (1)
- Windows (12)
- Windows 10 (3)
- Windows 2016 server (2)
- Windows 2019 server (1)
- Windows 7 (4)
- Windows (17)
- Windows 10 (3)
- Windows 2003 server (3)
- Windows 7 (3)
- Windows 2019 server (1)
- Wireless (6)
- Hardvér (1)
- Nástroje (4)
- Referencie (1)
- Wireless (2)
- Tools (2)
- Záverečné práce (5)
Current category:
CCNP
This example shows how to generate 254 loop interfaces with assigned ipv4 addresses 172.16.0.1/24 up to 172.16.255.1/24. The code is: enable tclsh for {set i 0} {$i < 256} {incr i} { ios_config „int loop $i“ „ip address 172.16.$i.1 255.255.255.0″…
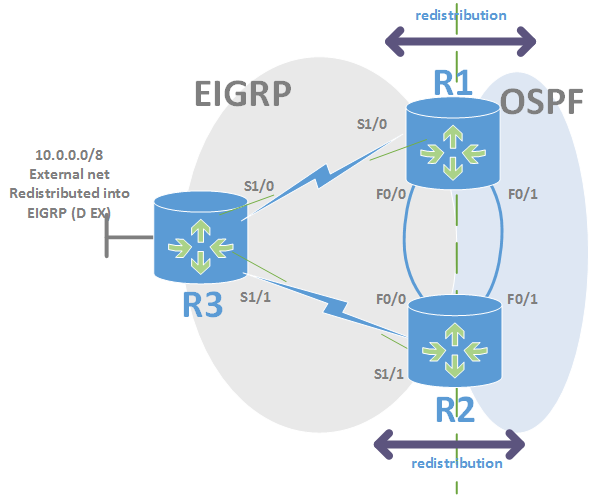
Teaching CCNP ROUTE courses and describing the problematic of two-way routing redistribution I need an example describing the case which point out to the process of creating a routing loop. This example shows how such routing loop may arise using…
We investigate a special topology condition, where a switch is connected itself on ports Faa0/1 and Fa0/2, and one of the port has BPDUFilter feature applied (i.e. simulating STP is switched off). Both ports are in the same vlan (vlan…
There is some confusion and misunderstanding regarding VTP (VLAN Trunking Protocol)+DTP (Dynamic Trunking Protocol) and this article will hopefully make it all clear. Most of the confusion comes from the statement that VTP is always a security threat to your…
Notes: Loki is a Python based framework implementing many packet generation and attack modules for Layer 3 protocols, including BGP, LDP, OSPF, VRRP and quite a few others. Web: https://www.c0decafe.de/loki.html http://www.ernw.de/content/e6/e180/e1561/Blackhat2010_ERNW_Loki_ger.pdf http://www.ernw.de/content/e6/e180/index_eng.html http://www.packetstan.com/2011/02/running-loki-on-backtrack-4-r2.html
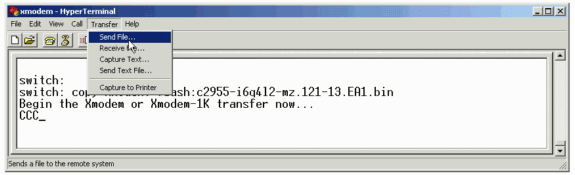
Sometimes in my lab happens that students delete IOS of the switch from its flash. Unfortunately switches does not have rommon to realize quick IOS recovery over tftp. Only one way is over Xmodem. To speed up the process of…
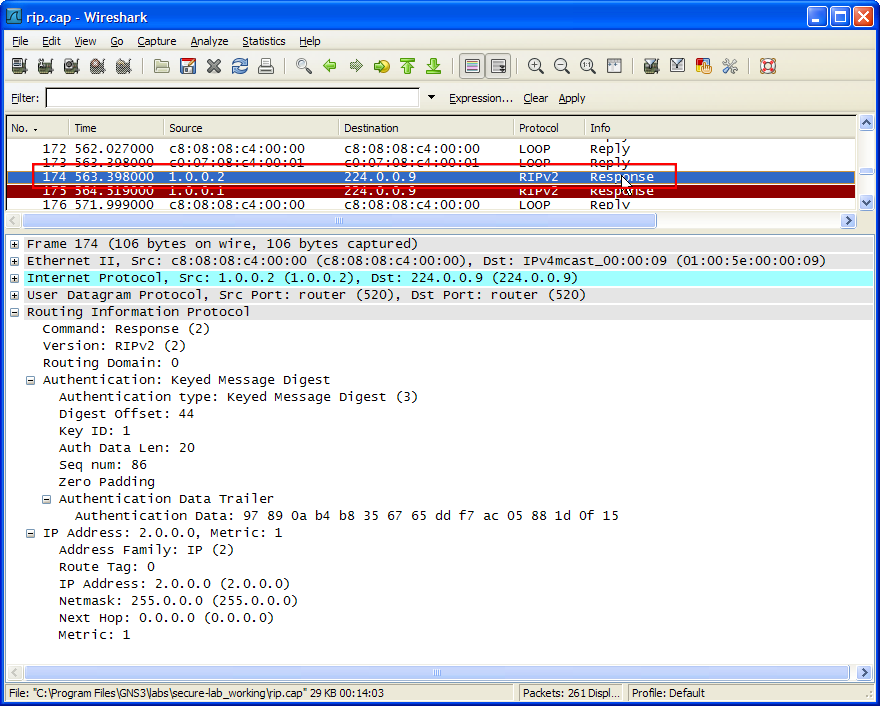
In this article I will configure, debug and shows the process of RIPv2 authentication. Authentication methods Plain text MD5 Note 1: When using plain text authentication mode, make sure that the following parameters are matching on neighboring routers…
The default configuration for the switch allows an end user with physical access to the switch to recover from a lost password by interrupting the boot process during power-on and by entering a new password. These recovery procedures require…